by Guest Post | Nov 8, 2019 | Cyber Crime, Sponsored Content, Web Security
Everyone who runs a website has heard of DDoS attacks and hopes never to see one at their doorstep. But, what do you really know about these attacks? Our perception can be muddied by several myths and misconceptions. Also, to efficiently protect one’s website from such attacks one needs to understand what they are. Let’s review the fundamentals.
Understanding DDoS attacks
A DDoS (Distributed Denial of Service) attack takes place when a hacker sends a lot of traffic to a particular website, essentially overwhelming it. The website server gets overloaded with these malicious requests and can’t function properly so it becomes inaccessible to visitors.
Perhaps you have seen situations when a website of some company can’t be accessed at the time of an important event or release connected to it (maybe it has even happened to you – and hey, there’s no shame in it; it has also happened even to Amazon). It occurs when the traffic is too high and the company’s servers can’t handle it.
A DDoS attack seeks to emulate such a situation, only without the pleasant (save for the headache that is fixing it!) feeling that you managed to draw so many people to your website.
In a sense, this type of attacks is somewhat similar to spam: flooding some resource with tons of undesired information and making it hard to find legitimate emails. Or, in this case, just crashing the website.
In a DDoS attack, the perpetrator gains access to computers or other devices that are connected to the Internet and uses their bandwidth to perform the attack. It is most often done with the users whose devices are being used for this purpose are not even aware. Usually, to hijack the device, the hacker needs to inject it with malware but it isn’t always so.
Sometimes, one can find themselves as a
part of a DDoS attack because of some seemingly safe activity they did online.
One example of that is the 2015 attack on 8chan. To gather their army of invading devices, the hacker bought bandwidth of the users of a popular VPN/proxy address provider through its sister company. Then, people who simply wanted to hide their IPs basically had them borrowed to commit a crime. While the use of that bandwidth to perform an assault on any website is illegal, buying and selling IPs is not. Those users should have read the terms of service which allowed it.
Since malicious traffic is coming from so many sources at once, it is nearly impossible to stop it and block all of it.
Why are such attacks carried out? The primary reason is money, as it’s possible to extort some from the unfortunate victim to stop the attack. On the other hand, sometimes DDoS attacks are performed just out of spite and to sow discord.
But why are DDoS attacks particularly
dangerous today, you might ask? The answer is simple. Just like with any
technology, modern Internet of Things devices that we all love so much can and
are used by bad actors for their purposes which often involve conducting
denial-of-service attacks on websites.
And the scariest thing here is the number of IoT devices. As of 2019, there are almost 27 billion of them worldwide. Moreover, the security of such devices is often lacking as their developers tend to focus more on functionality and, pardon the slang, oomph of their tools than on the questions of cybersecurity that are generally rather boring to the public and can’t be used in advertising as effectively. These two factors put together make our IoT environment something of a time bomb waiting to go off at some hacker’s prompt. The most famous example of an IoT-powered DDoS attack is, perhaps, the Mirai botnet one that happened in 2016.
How can DDoS attacks be prevented?
Most of the ways to protect one’s network or website from DDoS attacks rely on rapid detection. Speed is very important here because the faster the attack is blocked, the less damage it can do.
Detecting a DDoS attack can’t be reliably
done by a human specialist due to how much data they would need to sift through
and how rapidly. Therefore, technical methods have to be used. Of course, since
they are not operated by humans, they must be given some criteria to work with
and understand what qualifies as abnormal activity. Such criteria may include
certain IP addresses and IP ranges that are to be blacklisted, variations of
HTTP cookies, etc.
Once a likely attack is detected, it needs to be quarantined. Today, it is done via a cloud-based solution most of the time because hardware solutions are often too limited in their scope and don’t have enough capacity to deal with all malicious traffic coming with a DDoS attack.
There are various means of getting your
website rid of this undesirable traffic. Black-hole routing, for example,
routes it to a dead address that no host machine is assigned to, causing DDoS
traffic to be “dropped” there harmlessly.
“Scrubbing” data centers are another way of traffic filtering. All traffic coming to your website is transferred to such a data center where it is determined if it’s legitimate or not.
Another undoubtedly cool way to protect
your website from DDoS attacks is a very futuristic one. However, today, we
have technologies that weren’t imaginable just a few decades ago as something
that will be actually available to the mortals.
I’m talking, of course, of artificial intelligence and machine learning (AI and ML).
The main benefit of machine learning is that
it’s not simply a set of filters that legacy protection measures often provide.
It can, indeed, learn to see patterns that are common to something. What
interests us the most is that AI can be taught what a particular website’s
traffic normally looks like and notice any irregularities faster and more
efficiently than any human can.
However, unlike simple filtering
mechanisms, AI is not limited in it. It doesn’t need a strict set of filters to
determine if an attack is happening because just like a human being (at least,
in theory), it can recognize something it has never seen before (and hasn’t
been told by a human that this is a malicious attempt) as a threat.
All in all, there are many methods of
protection against DDoS attacks. Most of them come in the form of a service
that can be acquired from a security firm. And indeed, such protection is not
cheap. It is a difficult question if your website needs it and there is no
universal answer. Some sites are more likely to get attacked than others. Some
can afford to go down for a couple of hours while others can’t.
The choice is yours. But I hope that now you know a bit more about DDoS attacks and approaches to defend against them.
[Editor’s note: this is a contributed article. Information about the author is found below.]
Sam Chester is a co-founder of Cooltechzone.com, a website dedicated to online privacy and cybersecurity. His area of expertise includes data security and analytics, software, and Internet censorship. He is a staunch supporter of limiting the role of government agencies in the lives of the citizens.
by Mark | Jan 11, 2019 | ECommerce, Industry News, State of the Web, Web Security
As we begin 2019, we think this is a good time to focus again on the issue of privacy (especially as it relates to web applications). In a nutshell, one can think of privacy as the ability to control information about an individual or a group. This includes how the information is collected, shared, and used.
Last year, the European Union began enforcing GDPR (General Data Protection Regulation) on May 25. This legislation is designed to “Reshape the way organizations across the region approach data privacy.” (Quote from https://eugdpr.org/). This represented a major improvement (in our opinion).
Organizations such as noyb (none of your business) are researching enforcement options. You may recall their director, Max Schrems, was interviewed by the CBS News show 60 minutes in November, 2018. For example, they filed 4 complaints over “forced consent” on May 25, 2018 (against Google, Instagram, Facebook, and WhatsApp).
We can think of many instances where details are collected (often without full consent) and shared with others. If you have been paying attention to the news in the past few years, you already know this is an issue.
As a professional organization, we encourage adherence to privacy principles which include:
- Never collecting more information than is necessary to complete a given task.
- Keeping collected information confidential (and not sharing with other organizations without your specific permission).
We published our views on privacy on June 1, 2018. We ask that web professionals (and those who aspire to our profession and craft) take time to evaluate their role in protecting privacy as we begin 2019. We contend the U.S. lags significantly in the area of privacy protection (at least protection “with teeth”).
We are interested in what our readers and members think about this issue and look forward to your comments.
Best always,
Mark DuBois
Executive Director and Lead Community Evangelist
by Will Ellis | Jan 4, 2019 | Cyber Crime, Web Security
It’s hard to stay anonymous on the internet…
Between government surveillance systems and advertising tracking tools, your every move online can be monitored.
But if that’s the case, then why are hackers and cybercriminals so successful in their nefarious endeavors? Shouldn’t it be easy to watch their activity too?
In reality, hackers spend as much time designing their attacks as they do finding ways to stay below the radar. A single slip-up can result in the end of their malicious enterprise.
The list below covers the seven most common methods that hackers use to stay a step ahead of those chasing them.
1. Adding Layers of Virtual Machines
In movies and television, you’ll often see a supposed hacker using a basic Windows laptop to launch a major attack. That’s rarely how it works in the real world. Hackers usually operate on Linux machines and are careful to add extra layers of infrastructure between them and their operation.
Before beginning an attack, a hacker will likely connect through a series of virtual machines that are hosted in different regions of the world, acting as sort of a private cloud network. These access points are sometimes referred to as ghost machines and are replaced on a regular basis so that a hacker can cover their tracks.
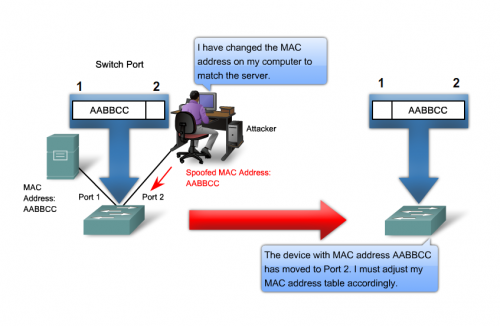
2. Spoofing IP and MAC Addresses

Every single device that wants to connect to the public internet must get an internet protocol (IP) address assigned to it by an internet service provider (ISP). This IP address will identifies the computer, tablet, or smartphone so that it can easily send and receive requested data from websites through a browser.
A media access control address (MAC address) is similar to an IP address except it is assigned during manufacturing and is specific to a network adapter. A computer with an ethernet port and a wi-fi access card will have two separate MAC addresses linked to it.
IP addresses and MAC addresses are the most common ways that people are tracked online. To get around this, hackers use a variety of tools to spoof addresses to disguise location and which devices they are using. Certain versions of the Linux operating system make it easy for a user to set a custom IP or MAC address.
3. Communicating With IRC
There’s a good reason you don’t see groups of cybercriminals talking about their enterprises on social media or message boards. Those types of forums are prone to eavesdropping and do not offer true anonymity.
Instead, you’ll find that most hackers rely on internet relay chat (IRC) implementations for all forms of communication. IRC apps are typically run on individual servers that do not interface with the public cloud. As a result, content on IRC channels is considered very secure and hard to trace.
4. Switching Between VPNs
When talking about internet security, virtual private networks (VPNs) are considered to be one of the smartest investments a person can make. With a stable VPN you can be confident that your internet activity is fully encrypted and protected from hacking.
But VPNs can be used for malicious purposes as well. In fact, hackers often maintain accounts with dozens of VPN providers and rotate between them on a regular basis. When it comes to choosing the best VPN service provider, it’s all about anonymity (ie, no logging). A properly functioning VPN connection will disguise a user’s true IP address, which makes it difficult to track their activity or determine their physical location.
In addition, some VPN providers offer an easy way to switch between access points. This means that a hacker can route their web traffic through a Canadian server one day and then move their activity to a German server the day after.
5. Using the TOR Browser
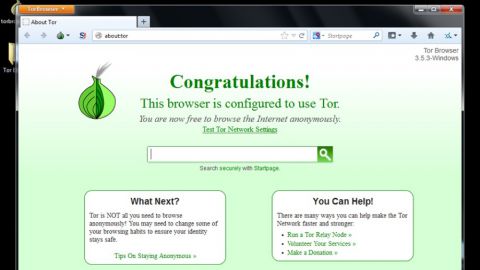
A typical internet user connects to websites using a popular browser application like Google Chrome or Mozilla Firefox. Hackers, on the other hand, have a different browser of choice. They primarily use a tool called the Tor browser, which offers built-in privacy advantages inherent with the great unindexed abyss that is the Dark Web.
When a webpage loads through the Tor browser, the initial request is actually first routed through a number of relays spread across the globe. This layered concept is known as onion routing, and that’s how The Onion Router became known simply as Tor.
At each stop on the onion relay, traffic is encrypted and then passed to a new IP address. This makes it almost impossible for outside entities to trace a user’s session and follow their activity.
6. Masking Email Addresses
Information that you share with another person over email might seem like a private communication, but that’s not the case for the largest email providers on the internet. These companies all have full access to the content of your messages, some of which may be used in government surveillance programs.
For this reason, you’ll rarely find an experienced hacker who relies on a Gmail or Outlook address, especially if part of their enterprise involves spam messages or other phishing attacks. Instead, like with IRC channels, they’ll host their own email server and use that exclusively.
Hackers have also developed a number of ways to mask their true email address when blasting large audiences with spam. Sometimes it’s as simple as adding a typo to an official-looking address that most internet users won’t notice. There are even services that offer temporary email addresses that expire after a certain period of time.
7. Encrypting Hard Drives
For a hacker, most of the focus is on network connections and covering their tracks on the internet. However, they also take careful steps to secure their physical devices. One of the most common ways is to use encrypted hard drives that require a special passcode to use.
In the fallout from a data breach, authorities may try to hack back and infiltrate the cybercriminals’ systems. Using an encrypted hard drive makes this almost impossible.
The Bottom Line
The point to all this talk about how hackers manage to stay clear of the long arm of the law is not to provide you, dear reader, with a primer on a new online crime career but rather to offer insight into how the bad guys stay out of sight.
The smartest thing you can do is take appropriate precautions to protect yourself with a VPN, updated security software, and a dose of common sense. Make no mistake, hackers are out there and you probably won’t see them coming.

by Harshala | Dec 21, 2018 | Cyber Crime, Web Security
Have you recently done a security checkup?
Cyber security is the practice of protecting systems, networks, and programs from digital attacks. These attacks are usually aimed at accessing, changing, or destroying sensitive information, extorting money from users, or interrupting normal business processes. Implementing effective cyber security measures is particularly challenging today because there are more devices than people, and attackers are becoming more innovative. People often use the same passwords on multiple accounts (and rarely change their passwords unless prompted). Since people are often the “weakest link” in a security program, one should periodically do a security checkup. This applies to individuals as well as organizations.
As you know, a security hacker is someone who seeks to breach defenses and exploit weaknesses in a computer system or network. Hackers may be motivated by a multitude of reasons, such as profit, protest, information gathering, challenge, recreation, or to evaluate system weaknesses to assist in formulating defenses against potential hackers. Once systems have been compromised or passwords leaked, access credentials are often placed on the “dark web.”

(more…)
by Will Ellis | Nov 30, 2018 | Cyber Crime, Web Security
Hackers and cyber criminals are constantly looking for new ways to trick internet users into exposing their personal and private data. These attacks are easier to execute than trying to infect an entire computer or local network, but the results can be just as damaging.
The term phishing applies to any instance where a message or website pretends to be part of a legitimate organization but in fact has malicious intent. Most begin with an email distribution, urging readers to click on a link and enter their passwords, social security numbers, or other identifying information.
When a person falls victim to a phishing scam, they may not realize the extent of the impact. Nowadays, stolen personal data is commonly sold on the dark web, a trend which will encourage more attacks in the future.
Even computer experts can sometimes be fooled by a phishing attempt, so it’s important to know what to watch for when opening your email and browsing the web. This article will describe the top five methods for quickly determining whether a website is real or fake.
1. Examine the URL Closely

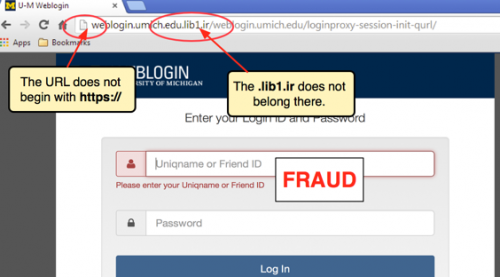
All websites on the public internet must use the hypertext transfer protocol (HTTP) with a registered domain name, which is the part of a web address that includes .com or .net. So when you first browse to a new website or click on an unfamiliar link, be sure to take a few extra seconds to review the URL in the address bar. If the address does not start with HTTP or HTTPS, close your browser right away as the site is unsafe.
Hackers will often buy domains that look like they are connected to a reputable company but actually redirect to a nefarious site. These addresses typically have misspellings in their name or use a different suffix.
Another trick that cyber criminals use is the disguising of a URL within a phishing email message. They may have a hyperlink that shows a familiar .com address, but when you click on it, the link will point to an entirely different location. When it comes to URLs, don’t trust anything except for what you see in the address bar at the top of your browser.
2. Check For the SSL Certificate
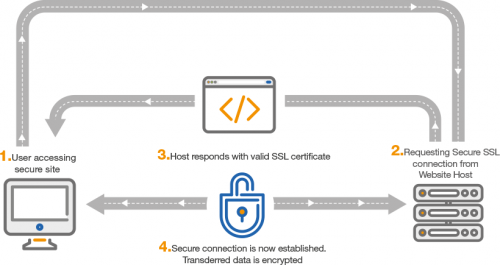
Websites with a secure sockets layer (SSL) certificate are equipped to handle requests over an encrypted connection. This means that all data sent between your browser and the website’s back-end servers cannot be decoded by any outside entities or hackers.
One of the first indications of a suspicious website is a missing or out of date SSL certificate. You can quickly check for this by looking at the left side of the address bar in your browser to see if a padlock icon is displayed. A simple padlock indicates a standard SSL certificate, while a green bar means that the website is using an extended validation SSL certificate, which offers some additional levels of security.
Modern browsers like Google Chrome and Mozilla Firefox will automatically warn you when you try to load a website that has a missing or expired SSL certificate. To be extra careful, you can click on the padlock icon to view the status of the certificate and the entity who registered it. Never submit any credit card transactions or other personal data through websites that lack an SSL certificate.
3. Scan Developer Tools
When you load a website’s contents into your browser, the HTML displayed in the window does not always tell the full story. In fact, the most dangerous part of phishing websites is often hidden in JavaScript and other code that is invisible to the untrained eye.
Fortunately, you can use the Developer Tools option in Google Chrome to scan for suspicious threats. To launch it, open the Chrome menu, go to the “More tools” submenu, and choose the “Developer Tools” option. A new panel will open with various tabs of information.
Perform a full refresh of the webpage and first check the “Sources” tab to see what external content is being loaded by your browser. Then do the same in the “Network” tab. If you see an unfamiliar domain listed in the logs, consider closing your browser and manually navigating to the website with a typed URL. You can even examine the webpage’s HTML and JavaScript code through the “Elements” tab.
4. Look for Contact Information
Reputable websites will either include their contact information in a dedicated page or else within the footer at the bottom of the HTML content. If you are unsure whether to trust the company with your sensitive data, consider checking these locations to validate the website owner’s identity. If you can’t find any contact information at all, chances the site is dangerous or poorly maintained.
Website footers also typically include a link to a privacy policy, which is a critical piece of information for internet users concerned about how their data is stored and who prefer that it not end up being hawked for a few bucks on the Dark Web. The policy will explain what kind of information is tracked by the website, how long it is kept, and what a user needs to do to delete it.
5. Query the Website Registration
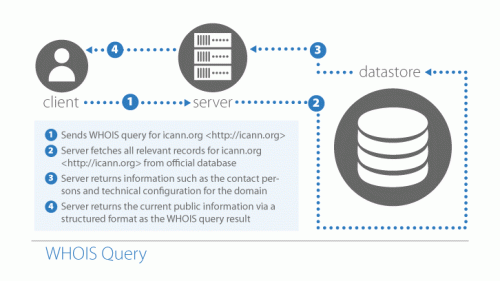
Upon purchasing any public domain name on the internet, whether it’s by an individual or a large company, the new owner must register it through the Internet Corporation for Assigned Names and Numbers (ICANN). Think of it like a DMV system for website registration.
This can come in handy when you want to check on the validity of a suspicious looking website. You can navigate to a ICANN lookup service and query any domain on the public internet with a WHOIS command.
The result of WHOIS query will indicate the legal name and address of website’s owner. It cannot tell you for sure whether a website is real or fake, but if the information provided does not look genuine or references a suspicious organization, you should avoid visiting the address entirely.
Final Thoughts
While phishers can be sneaky, the real problem lies in a gullible public or one too busy to take the time to learn how to properly vet websites. These tips we’ve just covered aren’t foolproof but can go a long ways towards ensuring you don’t hand over your credit card or other personal information to every hacker who throws a fake website in front of you.
It’s like crossing the road. Stop for a few seconds, look both directions, and make sure you have the lay of the land before proceeding. Good luck and thanks for reading.
Editor’s note: Will Ellis develops the guts beneath beautiful websites and can’t wait to see what the blockchain world will look like once the technology fully emerges. He invests in cryptocurrencies and studies history.


by Mark | Aug 31, 2018 | Web Security
Another week, another data breach
As we develop web sites and APIs, we need to keep security in mind. I know this is obvious, but it is also something often overlooked. It is not glamorous. It is not something that has perceived value by many in management. That is, until there is a security breach and associated bad publicity. Security vulnerabilities come in many different guises. Many have one thing in common – they were addressed many years ago. Yet, we often keep making the same mistakes on sites. We know how to fix many of these. We simply have not forced the idea that security must be incorporated into all our work processes. Just look at the OWASP top 10 vulnerabilities. Sure there are differences between the 2013 and 2017 versions, but there are many similarities as well. Cross site scripting remains a threat (as does SQL injection and many other vulnerabilities).

We all need to be thinking about security as we develop web applications. However, those teaching application development need to stress this in every project assigned. Unless security becomes ingrained in our application development process we will continue to repeat the mistakes of the past. And. Data breaches will continue.
(more…)









