by Will Ellis | Jan 4, 2019 | Cyber Crime, Web Security
It’s hard to stay anonymous on the internet…
Between government surveillance systems and advertising tracking tools, your every move online can be monitored.
But if that’s the case, then why are hackers and cybercriminals so successful in their nefarious endeavors? Shouldn’t it be easy to watch their activity too?
In reality, hackers spend as much time designing their attacks as they do finding ways to stay below the radar. A single slip-up can result in the end of their malicious enterprise.
The list below covers the seven most common methods that hackers use to stay a step ahead of those chasing them.
1. Adding Layers of Virtual Machines
In movies and television, you’ll often see a supposed hacker using a basic Windows laptop to launch a major attack. That’s rarely how it works in the real world. Hackers usually operate on Linux machines and are careful to add extra layers of infrastructure between them and their operation.
Before beginning an attack, a hacker will likely connect through a series of virtual machines that are hosted in different regions of the world, acting as sort of a private cloud network. These access points are sometimes referred to as ghost machines and are replaced on a regular basis so that a hacker can cover their tracks.
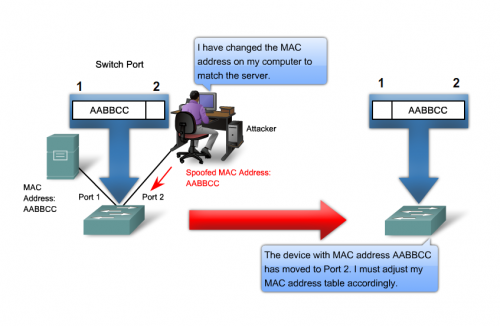
2. Spoofing IP and MAC Addresses

Every single device that wants to connect to the public internet must get an internet protocol (IP) address assigned to it by an internet service provider (ISP). This IP address will identifies the computer, tablet, or smartphone so that it can easily send and receive requested data from websites through a browser.
A media access control address (MAC address) is similar to an IP address except it is assigned during manufacturing and is specific to a network adapter. A computer with an ethernet port and a wi-fi access card will have two separate MAC addresses linked to it.
IP addresses and MAC addresses are the most common ways that people are tracked online. To get around this, hackers use a variety of tools to spoof addresses to disguise location and which devices they are using. Certain versions of the Linux operating system make it easy for a user to set a custom IP or MAC address.
3. Communicating With IRC
There’s a good reason you don’t see groups of cybercriminals talking about their enterprises on social media or message boards. Those types of forums are prone to eavesdropping and do not offer true anonymity.
Instead, you’ll find that most hackers rely on internet relay chat (IRC) implementations for all forms of communication. IRC apps are typically run on individual servers that do not interface with the public cloud. As a result, content on IRC channels is considered very secure and hard to trace.
4. Switching Between VPNs
When talking about internet security, virtual private networks (VPNs) are considered to be one of the smartest investments a person can make. With a stable VPN you can be confident that your internet activity is fully encrypted and protected from hacking.
But VPNs can be used for malicious purposes as well. In fact, hackers often maintain accounts with dozens of VPN providers and rotate between them on a regular basis. When it comes to choosing the best VPN service provider, it’s all about anonymity (ie, no logging). A properly functioning VPN connection will disguise a user’s true IP address, which makes it difficult to track their activity or determine their physical location.
In addition, some VPN providers offer an easy way to switch between access points. This means that a hacker can route their web traffic through a Canadian server one day and then move their activity to a German server the day after.
5. Using the TOR Browser
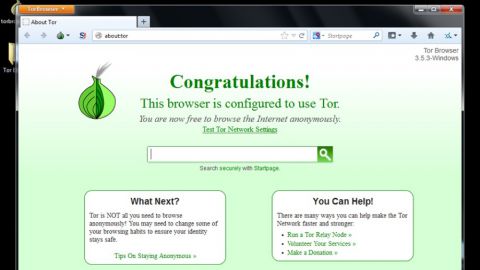
A typical internet user connects to websites using a popular browser application like Google Chrome or Mozilla Firefox. Hackers, on the other hand, have a different browser of choice. They primarily use a tool called the Tor browser, which offers built-in privacy advantages inherent with the great unindexed abyss that is the Dark Web.
When a webpage loads through the Tor browser, the initial request is actually first routed through a number of relays spread across the globe. This layered concept is known as onion routing, and that’s how The Onion Router became known simply as Tor.
At each stop on the onion relay, traffic is encrypted and then passed to a new IP address. This makes it almost impossible for outside entities to trace a user’s session and follow their activity.
6. Masking Email Addresses
Information that you share with another person over email might seem like a private communication, but that’s not the case for the largest email providers on the internet. These companies all have full access to the content of your messages, some of which may be used in government surveillance programs.
For this reason, you’ll rarely find an experienced hacker who relies on a Gmail or Outlook address, especially if part of their enterprise involves spam messages or other phishing attacks. Instead, like with IRC channels, they’ll host their own email server and use that exclusively.
Hackers have also developed a number of ways to mask their true email address when blasting large audiences with spam. Sometimes it’s as simple as adding a typo to an official-looking address that most internet users won’t notice. There are even services that offer temporary email addresses that expire after a certain period of time.
7. Encrypting Hard Drives
For a hacker, most of the focus is on network connections and covering their tracks on the internet. However, they also take careful steps to secure their physical devices. One of the most common ways is to use encrypted hard drives that require a special passcode to use.
In the fallout from a data breach, authorities may try to hack back and infiltrate the cybercriminals’ systems. Using an encrypted hard drive makes this almost impossible.
The Bottom Line
The point to all this talk about how hackers manage to stay clear of the long arm of the law is not to provide you, dear reader, with a primer on a new online crime career but rather to offer insight into how the bad guys stay out of sight.
The smartest thing you can do is take appropriate precautions to protect yourself with a VPN, updated security software, and a dose of common sense. Make no mistake, hackers are out there and you probably won’t see them coming.
by Will Ellis | Dec 14, 2018 | Content Strategy, Cyber Crime, ECommerce, Industry News
If you earn a living – or even just spending money – selling stuff online as an affiliate, you should be concerned about cookies.
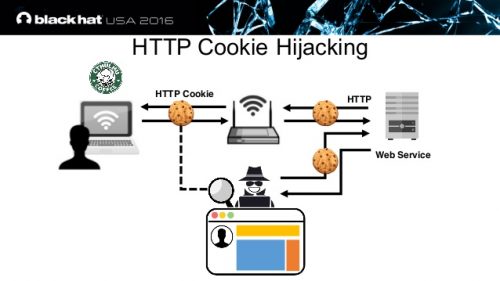
Digital cookies are the behind-the-scenes gizmo that credits you with a sale generated by a web page visitor. What you may not realize is that it is entirely possible for a clever hacker to hijack those cookies and end up with a sale that should have been credited to your account.
We’re talking big money. Shawn Hogan drew the attention of the FBI when he redirected around $28 million from rightful affiliates to his own account over the course of a few years.
The process in question is known as cookie hijacking or session hijacking.
To protect your cookies, it’s time to get serious about cybersecurity. It’s time to learn what cookies are, how they get hijacked, and what you can do minimize the risk.
Understanding Cookies
A cookie is a small packet of data that a web server transfers to a browser when someone visits a web page. Think of it as a message that originates with the server and is received by the visitor. Unless the visitor has blocked cookies, that data downloads onto the system and makes it easier for the page to load the next time the visitor returns.
That’s the main purpose of cookies: to make visiting a page simpler by ensuring it loads a little faster. It also helps the owner of the page have a better idea of how many visitors the page generates, if there are return visitors, and in general keep up with traffic patterns.
As it relates to affiliates, those cookies also make it easier for you to get credit when a consumer purchases something via your page.
How Can They Be Hijacked?
Cookies are dead simple, which may be why they are often overlooked as a means of committing a crime. All it really takes is for a hacker to seize the cookie and make a minor alteration.

The next time a visitor lands on your page the cookie ensures that the hacker’s content loads. In most cases, it will be an almost perfect mirror of the original page. What’s different is the packet of information downloaded for the session is not original. It’s been altered. That sets the stage for the hacker to control what happens next.
What Does this Mean For Affiliates?
Why would cookie hijacking matter to an affiliate? After all, doesn’t the visitor use the URL to get to the right place and make a sale? What does the cookie have to do with it anyway?
The thing to remember is that the cookies make loading the order page easier. If you alter the data in the cookie so that the affiliate ID is no longer the same, the credit for that order is redirected to another source. That’s because the cookie is often stored in the raw URL for the session. Alter the cookie by changing the affiliate ID and the end user doesn’t really notice anything.
In other words, it appears that the consumer is placing the order with you, but it’s actually being placed with someone different. You never get credit for the sale and certainly don’t receive a commission. That makes this little malfeasance a form of affiliate fraud.
How Do You Know If Your Affiliate Cookies are Hijacked?
Cookie hijacking is difficult to spot. In fact, it would be almost impossible to detect when it happens during a live session. Whether the session hijacking is active or passive, you only have a chance of identifying the damage once it’s done.
One sign that something is not right has to do with the performance of the web page. If it begins to function erratically for no apparent reason, that could mean something has been altered. Alternatively, the page shutting down can be an indication something has been changed. At this juncture, you may want to check the cookies related to the page closely and see if the affiliate ID or even some other aspect of the cookie code is not as it should be.
If your affiliate partner emails or texts you when individual sales occur, compare that information to the commission report. If they don’t match, and there’s no evidence of returns or canceled orders, someone else is ending up with your commissions.
Are There Ways to Prevent Hijacks?
Preventing a hijack is actually simpler on the visitor side. If the page visitor has up to date malware and antivirus software, the protections in those programs will likely spot that something was changed during a session. This gives the individual the opportunity to end the session before completing a transaction. The problem is the high rate of old malware and antivirus software in use.
Your affiliate can provide some support in terms of preventing cookie-jacking. Depending on how the servers download cookies and what sort of security is used for your customized affiliate page, it may be possible to prevent hacking software from modifying the cookies and the session ID that’s generated.
Create Your Own Encrypted Internet Connection
It’s not as complicated as it sounds. The concept of a virtual private network or VPN is coming into its own and likely will become an indispensable component of internet connections before too much more time has passed.
A VPN works in conjunction with your ISP. It is a separate service that encrypts the data that flows between your device and the internet. You don’t have to be a cryptographer to realize that encryption makes it harder for a hacker to complete his task. The extra ten or so bucks a month is money well-spent.
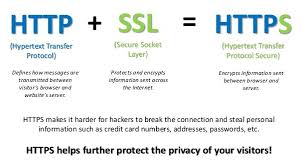
Make sure your affiliate pages use HyperText Transfer Protocol Secure (HTTPS) rather than HyperText Transfer Protocol (HTTP). Doing so adds another layer of protection by scrambling the code that’s shared between the originating server and the recipient
The Bottom Line
You don’t devote time and energy to building a business only to have someone else steal sales as certainly as if they reached over and grabbed twenty bucks from your wallet. Make it a point to educate yourself about online security. Subscribe to a blog or two. You don’t have to be a techie to stay updated on the latest threats and keep solid malware protection in place.
by Will Ellis | Nov 30, 2018 | Cyber Crime, Web Security
Hackers and cyber criminals are constantly looking for new ways to trick internet users into exposing their personal and private data. These attacks are easier to execute than trying to infect an entire computer or local network, but the results can be just as damaging.
The term phishing applies to any instance where a message or website pretends to be part of a legitimate organization but in fact has malicious intent. Most begin with an email distribution, urging readers to click on a link and enter their passwords, social security numbers, or other identifying information.
When a person falls victim to a phishing scam, they may not realize the extent of the impact. Nowadays, stolen personal data is commonly sold on the dark web, a trend which will encourage more attacks in the future.
Even computer experts can sometimes be fooled by a phishing attempt, so it’s important to know what to watch for when opening your email and browsing the web. This article will describe the top five methods for quickly determining whether a website is real or fake.
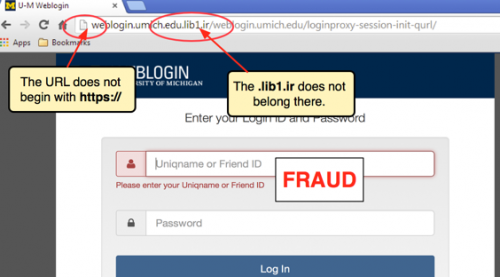
1. Examine the URL Closely

All websites on the public internet must use the hypertext transfer protocol (HTTP) with a registered domain name, which is the part of a web address that includes .com or .net. So when you first browse to a new website or click on an unfamiliar link, be sure to take a few extra seconds to review the URL in the address bar. If the address does not start with HTTP or HTTPS, close your browser right away as the site is unsafe.
Hackers will often buy domains that look like they are connected to a reputable company but actually redirect to a nefarious site. These addresses typically have misspellings in their name or use a different suffix.
Another trick that cyber criminals use is the disguising of a URL within a phishing email message. They may have a hyperlink that shows a familiar .com address, but when you click on it, the link will point to an entirely different location. When it comes to URLs, don’t trust anything except for what you see in the address bar at the top of your browser.
2. Check For the SSL Certificate
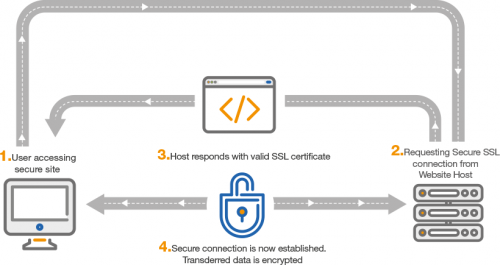
Websites with a secure sockets layer (SSL) certificate are equipped to handle requests over an encrypted connection. This means that all data sent between your browser and the website’s back-end servers cannot be decoded by any outside entities or hackers.
One of the first indications of a suspicious website is a missing or out of date SSL certificate. You can quickly check for this by looking at the left side of the address bar in your browser to see if a padlock icon is displayed. A simple padlock indicates a standard SSL certificate, while a green bar means that the website is using an extended validation SSL certificate, which offers some additional levels of security.
Modern browsers like Google Chrome and Mozilla Firefox will automatically warn you when you try to load a website that has a missing or expired SSL certificate. To be extra careful, you can click on the padlock icon to view the status of the certificate and the entity who registered it. Never submit any credit card transactions or other personal data through websites that lack an SSL certificate.
3. Scan Developer Tools
When you load a website’s contents into your browser, the HTML displayed in the window does not always tell the full story. In fact, the most dangerous part of phishing websites is often hidden in JavaScript and other code that is invisible to the untrained eye.
Fortunately, you can use the Developer Tools option in Google Chrome to scan for suspicious threats. To launch it, open the Chrome menu, go to the “More tools” submenu, and choose the “Developer Tools” option. A new panel will open with various tabs of information.
Perform a full refresh of the webpage and first check the “Sources” tab to see what external content is being loaded by your browser. Then do the same in the “Network” tab. If you see an unfamiliar domain listed in the logs, consider closing your browser and manually navigating to the website with a typed URL. You can even examine the webpage’s HTML and JavaScript code through the “Elements” tab.
4. Look for Contact Information
Reputable websites will either include their contact information in a dedicated page or else within the footer at the bottom of the HTML content. If you are unsure whether to trust the company with your sensitive data, consider checking these locations to validate the website owner’s identity. If you can’t find any contact information at all, chances the site is dangerous or poorly maintained.
Website footers also typically include a link to a privacy policy, which is a critical piece of information for internet users concerned about how their data is stored and who prefer that it not end up being hawked for a few bucks on the Dark Web. The policy will explain what kind of information is tracked by the website, how long it is kept, and what a user needs to do to delete it.
5. Query the Website Registration
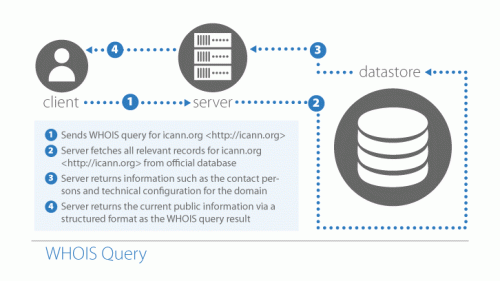
Upon purchasing any public domain name on the internet, whether it’s by an individual or a large company, the new owner must register it through the Internet Corporation for Assigned Names and Numbers (ICANN). Think of it like a DMV system for website registration.
This can come in handy when you want to check on the validity of a suspicious looking website. You can navigate to a ICANN lookup service and query any domain on the public internet with a WHOIS command.
The result of WHOIS query will indicate the legal name and address of website’s owner. It cannot tell you for sure whether a website is real or fake, but if the information provided does not look genuine or references a suspicious organization, you should avoid visiting the address entirely.
Final Thoughts
While phishers can be sneaky, the real problem lies in a gullible public or one too busy to take the time to learn how to properly vet websites. These tips we’ve just covered aren’t foolproof but can go a long ways towards ensuring you don’t hand over your credit card or other personal information to every hacker who throws a fake website in front of you.
It’s like crossing the road. Stop for a few seconds, look both directions, and make sure you have the lay of the land before proceeding. Good luck and thanks for reading.
Editor’s note: Will Ellis develops the guts beneath beautiful websites and can’t wait to see what the blockchain world will look like once the technology fully emerges. He invests in cryptocurrencies and studies history.











