
by Mark | May 31, 2023 | AI and Machine Learning, CSS3, JavaScript, Web Accessibility
Hard to believe we are almost at the middle of 2023. Time flies. As we prepare for our 20th national web design and development competition in Atlanta (beginning June 20), we thought it might be useful to share some of the articles we have been reading.
AI and images
Before we cover those articles, we feel it is important to mention our featured image. This was generated using Adobe FireFly. We used the following text to have the image generated. Note that we were rather specific in what we asked for (and the technology complied).
Looking at a desktop holding a phone, tablet and laptop along with a notebook with a pen. The desktop has one succulent plant. Sunlight is coming through a window to the left of the desktop.
If you expand the image, you will note that there is a tag assigned in the lower left corner indicating this image was generated using AI. We never cease to be amazed at how quickly one can create images (and how detailed they are).
We recently became members of the Content Authenticity Initiative. As we have mentioned in earlier weblog posts, the purpose is “to provide media transparency to allow for better evaluation of content.” We encourage readers to check out this initiative (and consider becoming members). In our view, as AI generated images become more prevalent, it is important to inform everyone that the image has been computer generated. We view this in a vein similar to copyrights. If one uses something that has not been created by the author, it is important to inform (and respect) where the images come from. That is why we commit to not only providing the source, but the text used to generate these images.
Accessibility
For those who missed it, May 19 marked Global Accessibility Awareness Day. The GAAD Foundation was launched in 2021 to mark the 10th anniversary. The focus is to make accessibility a core requirement. We encourage you to review the site (and focus on accessibility every day, not just May 19th).
CSS
We recently encountered a nice review of what’s new in CSS and UI. The article outlines 20 recent developments.These include responsive design improvements (such as container queries and style queries). The :has( ) selector lets one check if a parent element has specific children. There are many other enhancements which professionals can take advantage of (either now or very soon). We encourage readers to review the article to learn more about changes happening this year.
Also, we recently learned that scoped CSS is back. “Scoped styles allow you to contain a set of styles within a single component on the page.” We encourage readers to review the capabilities discussed in this article. Some nice examples are also provided.
We also came across this article (written in January) discussing new CSS relative units. Did you know there are roughly 50 CSS length units?
JavaScript
We recently encountered this nice overview of new JavaScript features coming in ECMAScript 2023. Many of these changes may have significant uses in your code. For example, change array by copy and array find from last. In addition to these smaller proposals, there are 4 larger ones. These include iterator helpers, temporal, decorators, and making resource management obvious.
National Web Competition
This year marks our 20th year of providing a national web design and development competition with SkillsUSA (yes, we started as a demonstration competition in 2004) and we have been running this ever since (even during the pandemic). We could not do this without the help of many people. We really appreciate their help and are posting additional articles. We managed to provide assistance to a number of states this year. We hope to see the winners of those state competitions at our national competition in June.
Feedback please!
That is what we found interesting this month. As always, we are keen to learn what you found interesting (and what you would like to learn more about). Please let us know in the comments.
by Mark | May 24, 2023 | AI and Machine Learning, Content Strategy
As readers know, we live in the age of significant disinformation. From political campaigns in various nations to recent untrue reports of an explosion at the Pentagon, such misinformation is meant to sow distrust, confusion, and other malicious intents. Given the rise of artificial intelligence (large language models) and the ease of creating images, video, audio and more, we at Web Professionals Global have joined the Content Authenticity Initiative. [Like all links, this will open in a new browser tab.] You might have to scroll a bit as there are now over 1,000 members of this initiative (organizations and citizens).
What is CAI?
Essentially, CAI (Content Authenticity Initiative) is a community of tech companies, non-governmental organizations (like Web Professionals Global), academics and others working to “promote adoption of an open industry standard for content authenticity and provenance.” What is the source of the image, video, audio in question? How was it created? If something has been tampered with, this is tracked and evident when examining the meta data. If you are not a member, we encourage you to join (either as an individual or a company). We are all about community (it is the first item in our tag line). We also believe strongly in copy rights as well as origin of media. CAI easily fits into our world view.
Not only will this help disprove misleading information, these tools can also help verify atrocities being committed. There are even apps one can include on a mobile phone which can be used to prove the provenance of any image taken by that device (and any subsequent manipulation).
An example (how to get started)
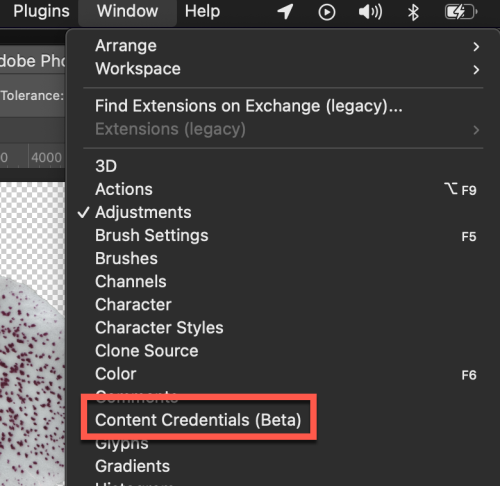
If you are using tools like Photoshop 2023 or Lightroom 2023, new capabilities exist to help with content. For our purposes, let’s use Photoshop. First, one needs to enable this beta capability. From the main menu, select Window > Content Credentials (Beta).

You then enable content credentials and link to your social media accounts. In this case, I have linked both our Twitter feed and Instagram feed. This provides and identifies references for individuals viewing your work.
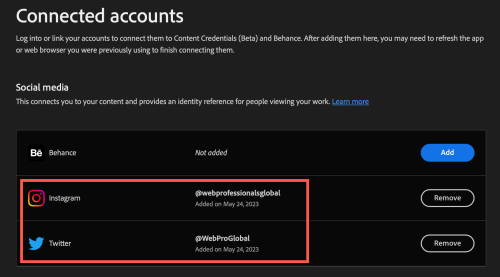
One can also choose to publish your content credentials to the cloud. The alternative is to attach them to your files (which would increase the file size of each file). When you refresh the Content Credentials panel, one would see the linked accounts in Photoshop.
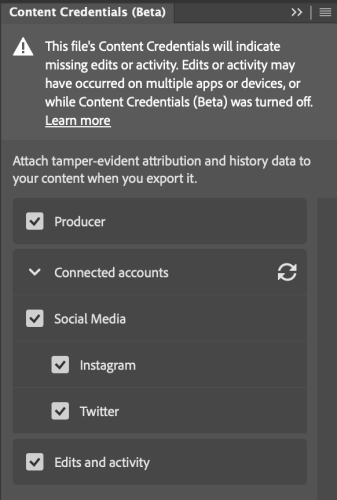
When you work with images, you can then preserve the content credentials as part of your file saving/exporting process. In this case, I removed the background from one of my orchid photos (generated by stacking a number of images together). Before exporting, these are some of the data one can include.
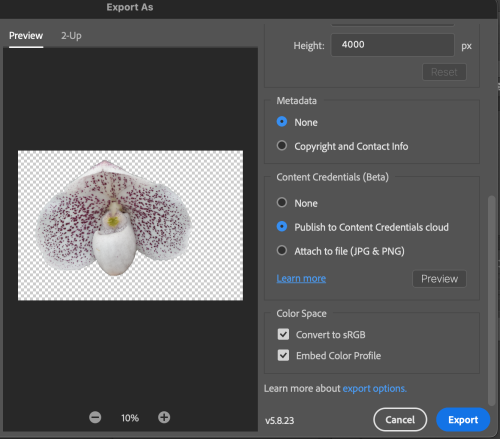
Ok, content credentials are now in the meta data. Now what?
Inspecting images
Perhaps one encounters the stacked image of an orchid online. We all know it is not possible to take a macro photo of a flower with such detail unless there has been some manipulation. One can use a tool like Verify (at the Content Authenticity Initiative site) to learn more about the image. Note that the image is being examined on your local computer (and is not being uploaded during this checking process). This is what I see when I examine the orchid image.
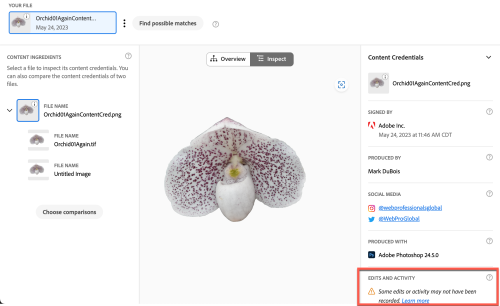
Note that there is recognition that there have been prior edits to this image (before the CAI was activated). However, one can also see the additional information. In addition to the inspection tab, there is an overview (for those who like to see the origins).
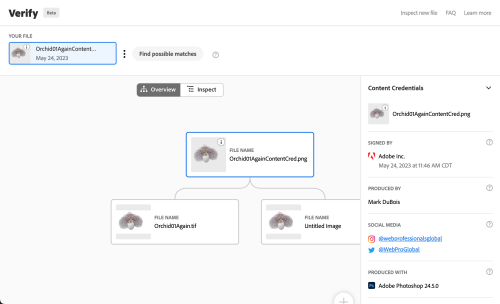
Of course, that was an overview of my efforts working with actual images. What about AI-generated images?
AI and C2PA
Tools (like Adobe Firefly) utilize open-source tools (C2PA in this case). If you follow the link to C2PA, there is an introduction video. Without going into all the weeds, here is what one sees when testing the content authenticity of a Firefly-generated image. Note, there is no visual overview as this was just machine-generated. One can clearly see the origin of the image.
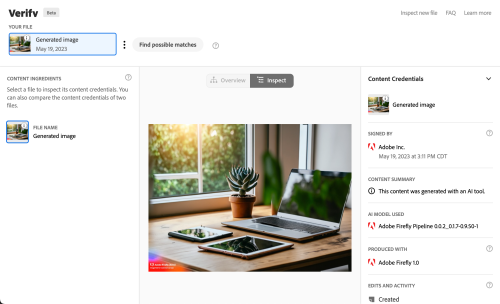
Perhaps the CAI will help us better deal with the wave of misinformation being generated. Time will tell. In the interim, we encourage you to try out these open-source tools. As always, we are curious what you think. Let us know in the comments.

by Mark | May 8, 2023 | AI and Machine Learning, Industry News, JavaScript
April has been a very busy month at Web Professionals Global. In addition to running the SkillsUSA national web design and development competition, we have been helping more and more states with their statewide web design and development competitions. This year we connected with a significant number. We provided the contest assets (including a work order), a coding environment, judging rubric, and associated videos to help both competitors use the online environment and judges review the work of competitors. This means our monthly update on what is happening in the world of the web is running a bit late.
Here are some of the articles we found interesting. We hope you enjoy learning more about what is happening. As always, we are interested in learning what you are most keen to learn about. Please add a comment and let us know. Here are some categories for the articles we found interesting. As mentioned in previous posts, all links will open in a new browser window/ tab.
- AI and current uses
- Browsers
- JavaScript
AI and current uses
You will note there is a featured image associated with this weblog post. In the past, this was manually generated (using tools such as Adobe Express or similar). The image this month was generate from a test entry describing to Adobe Firefly what was desired. In this example, I entered text asking for a photo of a desktop with an open laptop, an open notebook, pens and pencils on the desk and blooming orchids. The result is what you see. It was generated in under 10 seconds. Yes, AI saves time.
We have also been using AI to generate the client assets for our web competitions. Logo creation, text content, and more are all generated using AI (which saves us considerable time).
As an organization, we support the recently formed Content Authenticity Intiative. We encourage readers to follow the link to learn more about this important initiative.
Browsers
It appears Google is considering updating the venerable padlock depicting SSL sites.They are considering a variant of the tune icon. Read more about it on the Chromium blog. They present a solid rationale for making this change. For example, only 11% of those surveyed really understood what the padlock meant. As they mention, even the FBI mentions the lock icon is no indication of website safety. We are curious as to your thoughts about this change. It appears this will be coming to a Chrome browser near you one of these releases. Let us know your thoughts in the comments.
Speaking of browsers, in case you missed it, April 30 marked the 30th anniversary of the licensing of the web for general use and at no cost. 30 years. WOW. Yes, that was a pun.
One more article you may find of interest – the calm web: a solution to our scary and divisive online world. Karolina Szczur provides many thoughtful insights. She also offers practical ways one can get started. For example, stripping away unnecessary code and removing low quality content.
JavaScript
Although this article is over a year old, it might be worth reviewing (and pointing this out to aspiring web professionals – perhaps those you teach). A web components primer seems a good introduction to the topic. For those of you teaching web technologies – do you discuss web components? Why or why not? What are your thoughts about this article?
Your turn…
That is a quick overview of some articles we found intriguing. We hope you enjoy them as well. What did you find helpful? What would you like to learn more about? Please tell us in the comments.

by Mark | Apr 28, 2023 | Profiles Of Success, Web Design
We love to take moments to brag. Today we are boasting about a web design program at Massac County High School in Metropolis, IL. Penny Allen is one of our newest teachers, and already she is knocking it out of the park. Penny has a number of students who will be receiving their industry credentials this year. The first course completer is Nick Proctor, who is a newly minted Certified Web Designer Apprentice (CWDSA-apprentice). He is the first high school student in the state of Illinois to do so with the new Learn and Earn program. We are proud to welcome Nick as one of the newest members of Web Professionals Global.
As if that isn’t already enough, Nick has already designed the website for a local bakery, Miranda’s Delight. The Web Design certification process helped teach him the skills to build the site and he is now taking the website to the next level by consulting with search engine optimization (SEO) experts to learn how to get more people to see his site while searching online. Students like Nick are “future-proofing” themselves with international industry-recognized certifications from Web Professionals Global that they can take with them into their future educational and professional endeavors. With the changing world of work, having certifications to set yourself apart is more important than ever before.
Nick is a great example of the Learn and Earn model, in which industry professionals have underwritten certification costs for students around the country. Instead of teaching to a test, the Web Professionals Global approach is to teach learners by enabling them to gain real-world experience and build a portfolio they can take with them. Nick is developing a professional portfolio and already having an impact in his local community.
One of the great aspects of web design is that it is a growing and stable career field, and many designers work on their own. According to the job site Zippia, there are over 21,000 freelance web designers in the U.S. The growth rate of web design between 2021 and 2031 is expected to be 23%, far above the average rate of 5% for other professions.
We caught up with Nick and Penny to hear about their experiences with the Web Design course and certification.
Hear from Nick
What attracted you to wanting to be a web designer?
Well, really I think it was this class. I had never really considered web design until I started taking this class this year. It was always something that I was sort of interested in because I’m also really interested in graphic design and like video production. And I feel like those three kind of fall under the same category of creating things online. And this is probably the easiest form for me, because I’m not the most creative mind, I guess I’m a lot better at taking instruction and then putting it out on a piece of paper. And that’s kind of what this is, with graphic design. I really enjoy it and have fun with it. Although I don’t necessarily have an artistic mind, for some reason web design just comes naturally to me.
How do you feel about the idea that you’re actually earning industry credentials right now in high school?
It’s honestly kind of surreal, because I never assumed that I could, I guess achieve something like this while I’m still in high school. It seems like something that is out of reach for a high schooler, and then to have that opportunity and be going through it right now is really strange but cool.
How exciting is it that this certification has helped you realize some of your goals?
I think it’s really exciting. I’ve been trying to do this for years but never had success until now. So being able to work with a client, build the website and get a site host and then have a complete site is really cool. Having the certification is great because I can carry it with me in my future.
What was it like hearing from industry professionals?
Oh yeah, in the lessons the professionals really clarified a lot of the things that I was really confused about. And I think hearing advice from people who do this in their daily lives is really great. Obviously teachers help a lot, but sometimes you want to hear from people who actually work in that field. And hearing from multiple people gave me different perspectives on different concepts as well.
We hear that you’ve already started your web design business. Is that true?
Yeah, I’ve actually just finished my first client. I’ve published that website, actually, and it’s up right now. I am struggling with the SEO right now. I’m not exactly sure how search engine optimization works at the moment. But I’ve been researching that a lot today and yesterday, and I’ve got it published, I just need to get it out there really, for people to search it.
What do your parents think about the fact that you’re getting a certification while in high school?
They’re actually really impressed with it, because I guess I hadn’t properly explained to them that I was getting certifications until a couple months ago. I just kind of walked in the house with the certification. And my mom was like, where did you get this from? And I was, Oh, it’s my web design class that I’ve been taking for a couple months now. And I think she’s just really proud of it because I guess she didn’t know that my school offered something like that either. As far as I know, we don’t have other certifications offered at the school.

Hear from Penny
What does it mean to you to get your students “future-ready” (certifications, more than just tech skills, etc.)?
This certification gives students a way to make money now and not have to wait until they graduate. Most college students have to work in lower wage jobs while going to college and work long hours during the evening or late nights. This certification will give them the freedom to work when they want, making much more money while going to school.
What do you think of the Learn and Earn Model?
When I introduced the idea of the Learn and Earn model to my students, we talked about how industry professionals were going to underwrite the cost of the students receiving their certifications if they worked hard. I asked my students what they thought about the idea of doing the work and projects in lieu of an exam, and they agreed and said it was a better idea. With an exam they could just memorize a bunch of ‘stuff,” pass the test, and then immediately forget it all. However, this model means they actually have to learn it and use it! This encourages them to remember the material. We are all thankful to the partnership between Web Professionals Global and CTeLearning for this opportunity.
Become our Newest Member
Whether you are a teacher looking for industry certification opportunities for your students, a student in high school looking to advance your career prospects or a working professional seeking to develop new professional skills for a career change, we can help. Our international industry-recognized certifications prepare learners for in-demand 21st-century careers. Contact us today to chat about how we can help.
by Mark | Apr 10, 2023 | Member Profiles, Web Design
We recently received a message from Amy F., one of our Web Professionals Global members who used her Certified Web Designer Associate (CWDSA) certification to land a job with the leading company in North America that supplies sustainable steel products to construction and green energy fields. Let’s hear from Amy:
“Hi all, I am doing well! I used my Web Design certification to get hired at Nucor. I’m learning BIM (building information modeling) and steel detailing. I’m very grateful for the opportunity I had to earn my Web Design certification. I know getting my certification helped me tremendously to get my job and thrive in my new role!”
We are so proud to have helped Amy land a job that is utilizing her Certified Web Designer skills. Amy also earned our Remote Working Professional Certification, so she is ready to work either remotely or in a hybrid model. Amy is an example of how Web Professionals Global certifications prepare web professionals for exciting career pathways. Our membership includes students who are planning for their professional futures, working professionals who are developing new skills, and those who are making career changes. Again, congratulations to Amy. We look forward to following her career and welcoming others like her into our organization.
To learn more, below is the original Q&A blog article we did with Amy back when she first earned her Certified Web Designer Associate and Remote Working Professional certifications.
Today we are highlighting Amy F., one of our most recent Web Professionals Organization certification recipients. She earned her Certified Web Designer (CWDSA) and Certified Remote Working Professional (CRWP) certifications as well as an Ethics in the Workplace microcredential, all from the comfort of her own home. She can use these credentials and her robust portfolio of web design projects in future interviews with potential employers or as a base to launch her own business as a freelancer.
MyCAA—also referred to as the My Career Advancement Account— is a program that provides tuition assistance for courses and certifications to military spouses. Amy was able to utilize the MyCAA program, and we are proud to be associated with this program that helps military spouses succeed. We have worked with countless military members and spouses over the years to help them earn certifications, and they are always among our most driven and hard-working students. As a military spouse, Amy is a great example of why we offer online certification programs.
We caught up with Amy to ask about her experience taking courses and earning certifications as a working professional.
What initially attracted you to web design?
Coding reminds me of math in a way! The beauty of math is that it’s either right or wrong. I love that! As I learned about coding, I realized it has operations of its own, a set of rules that need to be followed. I find that relaxing.
As a military spouse, what did you enjoy about being able to complete the courses and certifications fully online?
I really appreciate that this class was fully online! I also liked the schedule flexibility as well as the ability to work on the certifications at my own pace and from wherever my husband and I were stationed at the time. We underwent a permanent change of station (PCS) move while I was in the middle of the courses, and I was able to continue working seamlessly.
How has taking the Remote Working Professional course and earning the certification empowered you as a working professional?
I’m fortunate that this course also offered a Remote Working Professional (RWP) Certification. I’m excited about the future and the jobs I will be able to get now that I have a RWP certification. I plan on working remotely so that I don’t have to look for work each time my husband and I change locations.
How has the Remote Working Professional course and certification changed your view of global connectivity and people being able to learn and work remotely from anywhere?
I love the fact that I can work for a company based anywhere in the world.
What skills did you learn in the Remote Working Professional course that you would share with a hiring manager in a job interview?
I learned a number of skills. To name just a few:
- Communication: well-mannered verbal and non-verbal communication as well as sending post-meeting recaps to avoid miscommunication are important.
- Organization: using a planner and setting a timeline.
- Ethics: adhering to commitments, showing empathy, and being respectful, honest, transparent, and accountable.
- Initiative: doing the job right and on time.
- Preparation: being ready for technology failures.
- Cultural sensitivity: understanding different cultural norms by researching before engaging.
- Cybersecurity: how to maintain safety and privacy.
How has your experience earning these certifications improved your confidence in being able to work from anywhere as a military spouse?
My mom and dad always tell me they’re proud of me…but that’s their job. I took the courses and earned the certifications so I could be proud of myself.
What advice would you give to others who are considering earning certifications to future-proof their careers?
The same advice my mom gave me: “The time is going to go by anyway!”
The internet, business, and marketing are all closely intertwined together—how do you think the courses and your new certifications will fit into your future plans as you go on to finish your business degree?
I will be graduating with my BBA this summer (woo-hoo)! Through my education I have earned experience, skills and qualifications that show I am capable of learning. After this summer, I plan to use my degree and certifications to land a nice job!
Mark DuBois, Executive Director of the Web Professionals Organization, said, “Amy is another great example of a MyCAA success story. I am proud of our military leadership for thinking about the whole military experience—not just for the service person, but for their spouses and families as well. I think it is a brilliant idea that we, as a country, invest in educational opportunities for military spouses. Our servicemen and servicewomen and their families sacrifice to maintain the security of our nation. Helping spouses gain marketable web technology skills so that they can move as duty requires helps make the family unit stronger and more resilient. MyCAA is money well spent. Everyone who has been a part of this program who has gone through the education and received certifications from us has been exactly the type of person employers want to hire. Congratulations again to Amy. We thank Amy and her husband for all they are doing to contribute to the safety and security of our country.” If you would like to earn certifications and learn skills that can make you a more marketable professional, check out our certifications list and contact us today. We would love to chat with you.

by Mark | Mar 27, 2023 | AI and Machine Learning, CSS3, Web Accessibility, Web Professional Trends
March has been a most interesting month in terms of new advancements in web design and development. Here are just a few articles we found interesting this month. Perhaps a bit of a directed stream of our thoughts supported by articles. Admittedly, some were published prior to March and we just encountered them. We encourage you to review these articles and follow along with the stream as we focus on:
- AI (and accessibility) – yes, they go together in many ways,
- CSS,
- JavaScript, and
- Website sustainability.
AI (and accessibility)
First, let’s examine a recent post by Brad Frost concerning “design systems in the time of ai.” As mentioned at the end of the article “…AI makes it crystal-clear we need to be focusing on why we create things vs what/how we create.” In a nutshell, AI can be used to improve efficiency in what is created. We can be leveraging the power of AI to reduce the mundane tasks and focus on what is important.
So, what does AI have to do with accessibility? It can help tremendously. Last year, Accessibility.com published a great overview of “How Artificial Intelligence is Improving Accessibility.” This is a rapidly evolving landscape, and we can think in terms of AI-supported voice assistants helping those with visual impairments, AI driven transcribing can help with those experiencing hearing impairment. Likewise AI tools can help with speech impairments (think in terms of Parkinson’s or brain injuries)as well as mobility impairments. We encourage you to read the linked article to learn more.
Accessibility
Focusing solely on accessibility, we found the Guide to Accessible Form Validation by Sandrina Pereira to be most informative. She correctly asserts that when we build form validations from scratch we often overlook accessibility. Sandrina focuses on both usability and accessibility. We found this article to be a solid introduction and encourage aspiring web professionals to develop such an approach in all their work.
We also encountered this solid article dealing with color contrast. Yes, this is something everyone finds very annoying. We liked the subtitle – “Web Accessibility for Text & UI Design.” Good thesis – always make your UI components easy to identify.
CSS
Getting started with style queries by Una Kravets is a solid read also. The ability to query a parent object’s inline size along with container query unit values has achieved stable support in modern browser engines. Una covers the fundamentals of working with these and provides useful examples (including code snippets). Of course, this technology continues to expand and you should be come familiar with these approaches whether you are a practicing web professional or an aspiring one.
JavaScript
Sandworm audit is a command line tool to identify vulnerabilities, malicious scripts, license, and metadata issues. It is free and open source and works with any JavaScript package manager. Have you tried it out? What are your thoughts?
For those who like a bit of spice with their JavaScript, we encountered Jared White’s “Great gaslighting of the JavaScript Era” article. This article represents a cogent view of many of the internal discussions we have been holding for several years. The web is built on standards and protocols. Your site is based on HTML, but can be served from any operating system on any hardware any place on our planet. You do not need a JavaScript framework to build a simple website. We seem to have forgotten that. Yes, I have personally seen sites relying on large JS libraries to display what could be done in a few lines of HTML (and stuled with a bit of CSS). Good article (and we agree with you Jared). This article is also a great segue to the issue of website sustainability (see below).
Website Sustainability
Alexander Dawson published an interesting article on the carbon impact of web standards in January, 2023 (yes, we just encountered this one and it is worth reading). Given that the Internet is a major source of carbon pollution, it is important to think in terms of sustainable web design. Yes, Greenpeace recently reported that if the Internet were a country, it would be in the top 10 carbon emitters. The BBC published an overview of the extent of the problem a few years ago. Yes, the WWW is highly dependent on electricity (and the source of much of that electricity is not carbon neutral). Alexander focused on HTML and CSS and how much energy was required to render a basic boilerplate. He relied on different browsers, different hosting providers, different equipment and different locations (among other variables).
His test suite consisted of nearly 300 HTML elements and attributes, over 500 CSS rule, selector, and property tests, and over 50 media and other specification tests. He noted that embedding interactive content caused the use of a significant amount of CPU, GPU, RAM, and data usage. Non-standard code triggered rendering issues as well. with respect to CSS, animation (specifically keyframe animation) and the use of custom fonts caused a dramatic impact. For media formats, SVG is the best. We thought his conclusion (below) summarized that major changes are needed.
Existing evidence shows that websites are getting more bloated [54], sites remain largely inaccessible [55], and with JavaScript taking higher importance than basic semantics in tooling practices, the backbone of the web (HTML & CSS) have become clogged with un-performant code. The existing web needs a firm shake-up if it is to meet it’s commitments to become sustainable (and user-friendly).
Your thoughts?
Yes, that was a lot to examine this month. We are keen to learn what you liked and what areas you would like us to examine in greater detail. We look forward to your comments.

by Mark | Mar 21, 2023 | Web Competitions
We are working closely with a number of states this year to help them better align their state SkillsUSA web design and development competitions with our national SkillsUSA competition to be held in Atlanta. Although our calendar is rather full, we are still willing to help additional states (if they request). Just contact us as soon as possible.
Contest overview
We provide the overall environment, assets, detailed scoring rubric, and online testing environment. We do ask that each state provide a contest supervisor (physically present the day(s) of the competition and judges who have knowledge of web design and development. We offer this overview of the contest:
- You will do all of the coding in an online editor environment.
- All teams will be given the same wireframe to implement.
- You will decide the colors, fonts, spacing and other aesthetics for the client and implement the aesthetics into the provided layout.
- The ‘client’ has provided images and content.
- As is often the case in the real world with assets provided by clients, they may not be completely appropriate for the web.
- You should rename and optimize images. You may adjust and add effects to fit your aesthetic vision.
- You are not allowed to use frameworks such as Bootstrap or jQuery or React. You must be able to demonstrate competency with the foundational technologies, HTML, CSS, and JS in this competition.
- Judges will use any or all of the latest versions of the following browsers
- Desktop: Chrome, Firefox, Safari, Edge
- Android: Chrome
- iOS: Safari on iPhone and or iPad
- Accessibility: JAWS screen reader or Apple VoiceOver
Coding Environment
We create the virtual coding environments for use by each team. We encourage competitors and judges to familiarize yourself with the coding environment prior to the competition: https://webprofessionals.site/IDEoverview (this link will open in a new browser tab). Obviously, it takes us a bit of time to spin up the individual environments for teams (which is why we ask for as much advance notice as possible).
External Resources
We are often asked if competitors can use external resources. Of course, but there are limits as we want as consistent an environment as possible (so judges can better evaluate similar work).
You will be allowed to use Google Fonts to find a font that is appropriate for the client. (https://fonts.google.com/) (this link will open in a new browser tab).
If you need textures or other design assets, you may find resources from the internet during the competition. They must have appropriate copyright licensing and sources will need to be documented. It is up to the competitor to confirm appropriate copyrights are followed (judges may likely check – disqualifying teams who do not follow copyrights).
You will need to find or create iconography for the client. We recommend https://thenounproject.com/ (this link will open in a new browser tab).
For those who would like to distribute a copy of this information, we provide a PDF version of this document.

by Mark | Feb 27, 2023 | CSS3, Industry News, JavaScript, Web Development
Here are some of the articles we have been reviewing during the month We hope you find them as interesting as we did. [Note: these links will all open in a new browser tab.] Don’t forget to let us know what else you would like to see in terms of current professional trends in web design and development. Here are the categories of what we encountered during February:
- CSS
- JavaScript
- Web Development Trends
CSS
Here is an interesting read – 10 modern layouts in one line of CSS. These include sidebar says, the pancake stack, the 12 span grid and much more. Let us know what you think of these.
If you are curious where CSS is going, consider the high definition CSS color guide. With Chrome 111, there is support for CSS Color 4 gamuts ( size of something) and color spaces (this is explained in much ore detail in the linked article). This means there is 50% more colors in supporting browsers.
Native CSS nesting may also be finally arriving (in Chrome 112, for example). Bryce Wray provides a nice overview of recent experiments with this.
JavaScript
Did you get a chance to review the state of JavaScript in 2022 article? In a nutshell, JavaScript is more vibrant than ever. Of course, there are many more details to be found in the linked article.
Web Development Trends
Robin Wieruch published an interesting overview of 10 web development trends in 2023. Among the trends discussed is a movement from client side rendering to server side rendering. It is worth noting that server side rendering is now relying on JavaScript. Serverless functions continue to be a trend this year.Because of this, databases are also experiencing a renaissance. In terms of JavaScript runtimes, Deno is a successor of node. To learn more about these trends (and much more), we recommend reading the entire article.
Horror stories
As professionals, we are always working with clients. We thought it might be helpful to share a horror story or two each month. Obviously, there are lessons to be learned. However, the fact that we have been using web technologies over three decades and still see some problems repeating means we are not fully learning these lessons.
Case in point. I was helping a client with a WordPress site. They had recently purchased a plugin and were experiencing difficulty in using the enhanced features which came with the upgraded plugin (freemium model is still very popular, isn’t it). Specifically, I was asked to investigate why all the added functionality remained greyed out despite having paid for the upgrade. To keep the story short, one had to click on the greyed out item to “load” the enhancement. Took yours truly about an hour to figure that one out. Lesson we should all have learned by now – there are standard design patterns which must be followed. To show something as greyed out means it is not active and not available. Breaking a pattern which has been in use for well over a decade causes unnecessary consternation. A simple explanation that one must click on an item to activate it might have sufficed (instead of wasting the time of multiple individuals).
As if that wasn’t enough, when helping another client, I needed to contact technical support for a WordPress plugin. Believe it or not, the individual who was trying to help me quickly asked for my username and password so they could access the site as an administrator to see what the problem was. Ummm, NO. Ok, they then asked if I could create a separate administrator account for them to use so they could see the site. Ummm. NO again. Think about this from a security perspective – if you allow someone (who you don’t know) administrative access to your site, you have handed over the data and capabilities of the site to a stranger. Would you gladly hand your car key fob to a stranger who asked for a ride to the store while you were waiting for the light to change? Maybe if your car was making a strange noise? Same concept. Never, ever, provide such access no matter how severe you think the problem is with a WordPress plugin. If you need that much help, it is time to find an alternate plugin. Shame on the vendor in this case for even allowing an employee to make such a request.
OK, readers, that is enough on the horror stories for this month. Do you have something you would like to share which tops these horror stories. Please let us know in the comments (or send us an email to our membership email at the top of the page). We are always interested in what you liked and would like to see in future articles. Just let us know that as well.
In case you missed these…
We recently published additional information about the proposed Websites and Software Applications Accessibility Act. We encourage you to review this post to keep up to date with what is happening regarding website accessibility.
Curious about security (especially passwords), please review our passwords and psychology article.
We also announced our 2023 web design and development competitions (including that we are recognized as a SkillsUSA Official Partner.
Your turn
We are always what you find interesting and what you would like to learn more about. Please provide comments below so we can better address what you find most interesting.

by Mark | Feb 10, 2023 | Web Design, Web Development, Web Pro Education, WOW News
We are proud to announce our new and streamlined for states to use for their SkillsUSA web design and development competitions in 2023. This model is based on over 20 years of running web design and development competitions (including 2 decades running the SkillsUSA national web design and development competition – which started as a demonstration competition in 2004). With the COVID-19 pandemic, we gained significant insights in running this competition 100% virtually. We have employed this knowledge as we enhanced our model for 2023. We are also proud to announce that we have been recognized as an official partner of SkillsUSA for 2023.
Alignment
We have been working with SkillsUSA for over two decades because of how much we are aligned in our vision of workplace needs. The SkillsUSA framework focuses on technical skills in addition to personal skills and workplace skills. This is the exact mix we strive for in our competitions. It is important to know the technical aspects of your trade, and it is equally important to work well in a team environment and follow ethical standards. This is also why we ask readers of our articles to sign our code of ethics (for members and non-members).
Our Internet based competition
This refreshed competition model is the most accessible it has ever been, enabling students to focus on creating innovative projects and equipping facilitators to run the competition seamlessly. Students only need a PC, Mac or Chromebook and an internet connection to participate in the competitions—giving those in rural, urban and suburban areas equal access.
Competitions can be run entirely online, which levels the playing field for students across the country and can give you flexibility should you need n the age of COVID-19 . This new competition model is future-proof and will be able to be implemented for years to come, no matter what the pandemic looks like in coming years.
Our (Web Professionals Global) competition support is free to state SkillsUSA competitions, and the new model makes the judging process more standardized and easier than ever before. States can run competitions whenever they want in 2023 in anticipation of our national competition in June in Atlanta. Please give us time to get your state setup with our online IDE (Integrated Development Environment), online exam, and online competition materials. Obviously each state will need Internet access during the day of competition for all competitors.
Not only does our new approach make it easier for any state to run their own web design and development competition, but it also ensures that every state is conducting their own competition that models the expectations their competitors will need to meet at our national competition. This gives every state — from small to large — the same turnkey resources to ensure a successful competition. This model is intended to only be used for the current cycle of SkillsUSA competitions.
Highlights
This new model includes:
- Competition project with all graphic and textual assets that are similar in scope and style to what the competitors will experience at the national competition.
- Easy-to-apply rubrics help both new and veteran judges quickly evaluate team projects for creativity, design and best practices.
- Web-based coding editor and folder system allows judges to easily review any state competitor submissions. Judges can review work with just an internet connection, allowing states to have judges join virtually from anywhere.
- Web-based editor and site storage means your events committee does not have to worry that any competitor’s work can be lost or misplaced—all of it remains safe on the web.
- Judging preparation materials and training videos are included to make it easy for new judges to quickly get up to speed and be able to deliver consistent judging.
- Optional competition kickoff and welcome video delivers a consistent message to all competitors as well as some helpful hints about the competition project.
- Technical back up and support provided by our Web Professionals Global Organization.
- Fast and easy sign-up for state SkillsUSA leadership teams to reserve their free competition kit and web-based tools suite.
Contact us now
Because of these new systems Web Professionals Global is implementing for this year, any state can run a turnkey competition and give students an opportunity to build meaningful projects in an engaging online environment. All of this is provided free of charge to any state wishing to have an organized and impactful state-level web design and development competition to prepare their students well for the national competition.
Let us know as soon as you can. As you can imagine, there will be many states taking advantage of all this support, and we need time to be able to deliver all that you need.

by Mark | Jan 31, 2023 | CSS3, HTML5, JavaScript, Web Security
Hard to believe January is almost behind us. Yes, time flies. As Executive Director, I am now in my 31st year of working with web technologies (yep, started in 1992). Obviously a lot has changed over three decades. And things continue to change at a rapid pace. Since it has been 3 decades, I found it entertaining to review the site focusing on web browser engines from 1990 until today. Nice bit of history for those who want a refresher (and for educators). [Note: these links will all open in a new browser tab.]
OK, now that the past is behind us, let’s see what is happening with the following web technologies (a few articles which caught my attention in these areas).
- CSS
- HTML
- JavaScript
- Security
CSS
If you are using CSS animations, you might consider AnimatiSS (a collection of CSS animations for your web project).
I also enjoyed reading more about the :has() pseudo-class including real world examples.
When working with media queries, I like the MediaQuery.style site. It has many of the more commonly employed ones readily available.
Although this is still a work in progress, the CSS fingerprint site demonstrates how one can use CSS (and only CSS) to track visitors. It is not really scalable as it presently requires over 1 MB of CSS downloads. However, it is an interesting concept. It does avoid technologies such as NoScript.
HTML
Yep, there are still changes happening to markup and tags. After much discussion, there has been some consensus on how to best use the dialog element. Actually, how it should handle its initial focus. You can read more at the post titled “Use the dialog element (reasonably)“. Note that this may not be implemented in all browsers, but it should be in subsequent releases of said browsers.
JavaScript
For those teaching JavaScript, you might find the beginners guide to Chrome tracing useful. Sometimes a DevTools trace is not enough.
I also came across this interesting article explaining why using document.write() is not always a good idea. It is fairly in depth and explains why the placement of suck code matter as well.
Security
Microsoft recently published their 2022 Digital Defense Report. You can follow the link to read much more. Here are some of the highlights (scary though they are).
- 921 password attacks happen every second (up 74% from last year).
- they blocked 37 billion email threats last year.
- Attackers are leveraging vulnerabilities in IoT device firmware to gain access to corporate networks.
- The average cost of a data breach reached $4.35 million.
- People are now the primary attack vector. Identity driven attacks account for 61% of breaches. Phishing remains the most common form of cyber attack.
Your thoughts?
These are some of the articles I have encountered and found interesting over the past month. What have you found in addition? We look forward to your comments and insights.
















